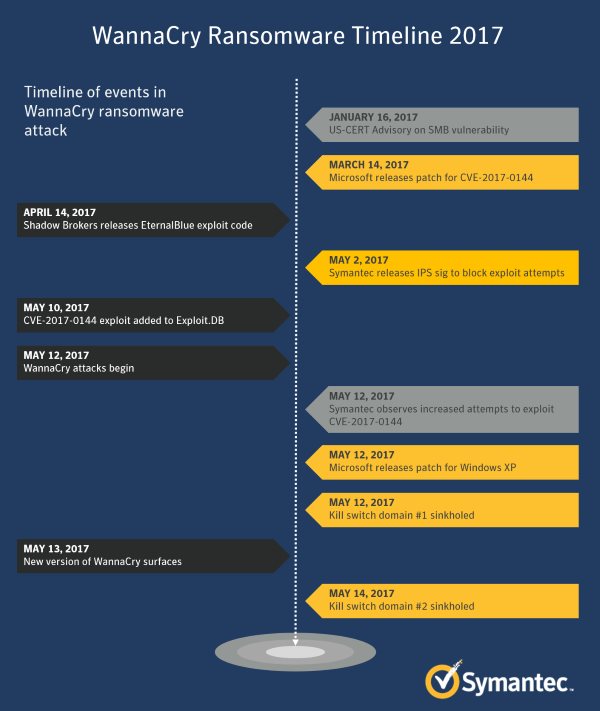
You know by now that your company could not survive without the Internet. Not in today’s market. You are either part of the digital economy or reliant upon it. With critical information assets at risk, your company requires a state-of-the-art cybersecurity program. But how do you achieve the best possible program? Tari Schreider, in Building Effective…